GitHub users targeted by Sawfish phishing campaign
GitHub users beware: online criminals have launched a phishing campaign to try and gain access to your accounts.
The Microsoft-owned source code collaboration and version control service reported the campaign, which it calls Sawfish, on Tuesday 14 April. Users were reporting emails that tried to lure them into entering their GitHub credentials on fake sites for a week before, it said.
The phishing campaign lures victims to domains that look similar to GitHub’s at first glance but which the company doesn’t own, such as git-hub.co, sso-github.com, and corp-github.com, the company said. Other domains misspell the ‘i’ in GitHub with an ‘l’, like glthub.info. The attacker also tried domains that look like those owned by other tech companies, such as aws-update.net and slack-app.net. Most of these domains are already down and the phisher has been swapping them out quickly, GitHub warned.
The phishing emails – which aren’t always well-written – try to raise the recipient’s alarm by suggesting that there’s something fishy going on with their account. One example, received on 4 April, asked a user to review their account activity:
It then took the user to this fake site, with a domain that GitHub says is associated with the Sawfish campaign:
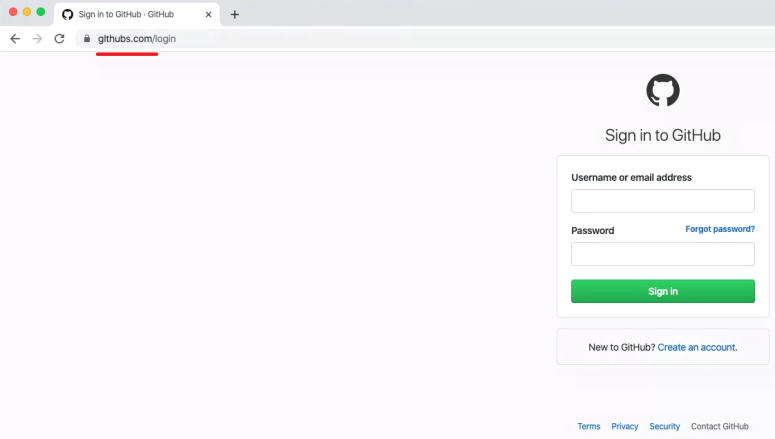
The phishers appear to be targeting people based on the addresses used for public Git commits. These are updates to source code that are publicly viewable. That could explain one Redditor’s report of a phishing email sent to an address used exclusively for GitHub.
Attackers use several techniques to hide the real link destination, including URL shorteners, sometimes strung together to make it even more difficult to see the ultimate destination. They also use redirectors on compromised sites that have a legitimate-looking URL but which then send the victim to another malicious site.


